By Eric Beach & Adam Marcus
Among Internet users, there are a variety of concerns about privacy, security and the ability to access content. Some of these concerns are quite serious, while others may be more debatable. Regardless, the goal of this ongoing series is to detail the tools available to users to implement their own subjective preferences. Anonymizers allow privacy-sensitive users to protect themselves from the following potential privacy intrusions:
- Advertisers Profiling Users. Many online advertising networks build profiles of likely interests associated with a unique cookie ID and/or IP address. Whether this assembling of a "digital dossier" causes any harm to the user is debatable, but users concerned about such profiles can use an anonymizer to make it difficult to build such profiles, particularly by changing their IP address regularly.
- Compilation and Disclosure of Search Histories. Some privacy advocates such as EFF and CDT have expressed legitimate concern at the trend of governments subpoenaing records of the Internet activity of citizens. By causing thousands of users' activity to be pooled together under a single IP address, anonymizers make it difficult for search engines and other websites--and, therefore, governments--to distinguish the web activities of individual users.
- Government Censorship. Some governments prevent their citizens from accessing certain websites by blocking requests to specific IP addresses. But an anonymizer located outside the censoring country can serve as an intermediary, enabling the end-user to circumvent censorship and access the restricted content.
- Reverse IP Hacking. Some Internet users may fear that the disclosure of their IP address to a website could increase their risk of being hacked. They can use an anonymizer as an intermediary between themselves and the website, thus preventing disclosure of their IP address to the website.
- Traffic Filtering. Some ISPs and access points allocate their Internet bandwidth depending on which websites users are accessing. For example, bandwidth for information from educational websites may be prioritized over Voice-over-IP bandwidth. Under certain circumstances, an anonymizer can obscure the final destination of the end-user's request, thereby preventing network operators or other intermediaries from shaping traffic in this manner. (Note, though, that to prevent deep packet inspection, an anonymizer must also encrypt data).
How Anonymizers Work
A Simple Anonymizer
An anonymizer is an intermediary server between the end-user and the website that acts as a proxy for the user, effectively accessing websites on the end-user's behalf, thereby hiding the end-user's IP address (and perhaps other information).
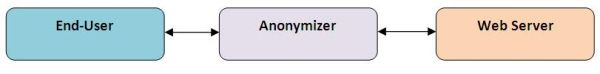
A Real-World Analogy: Let's say I want to order pizza from the local pizza shop, but I do not want them to have my phone number, which they could get from caller ID if I called them directly. Instead of calling them myself, I could call a friend and ask him to call them on my behalf, place my order, and then let me know how much it will cost and the estimated delivery time.
A Somewhat More Complicated Anonymizer Setup
A more sophisticated (and more realistic) anonymizer setup pools hundreds or even thousands of end-users through one or more anonymizing intermediaries. Consequently, web servers receive requests that originated from hundreds of end-users through a single IP address (that of the anonymizer). As a result, the web server is unable to distinguish and personally identify the IP addresses of any users.
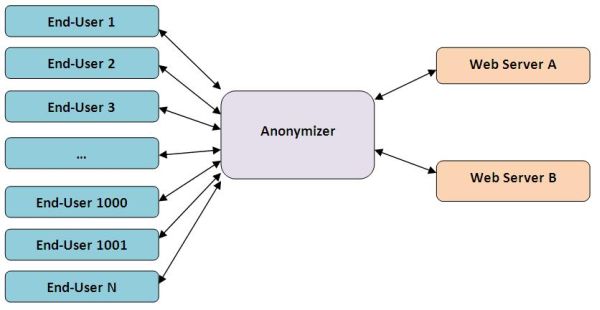
An Even More Complicated Anonymizer Setup
The above setup provides a layer of privacy beyond the traditional setup of direct end-user-to-website communication. But even so, if the anonymizer's logs are compromised, so too is the privacy of the end-user -because it will likely be possible to associate specific requests with individual users.
A much greater degree of privacy protection is obtained by "daisy-chaining" together multiple anonymizers, but every additional hop slows down the browsing experience and leaves additional traces of the end-user's traffic.
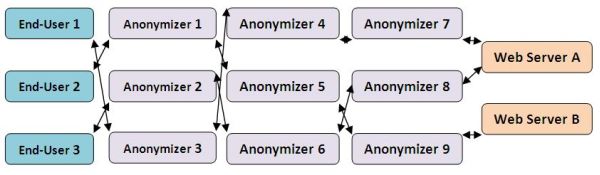
How Do I Set Up an Anonymizer?
A variety of anonymizer services exist. Due to considerable variations in how each is installed, it is impossible to provide universal step-by-step details for installing one. But perhaps the two most trustworthy (free) options are Tor and Privoxy. While both services have experienced occasional vulnerabilities and hiccups, they are the best established among anonymizers. Other providers include: CGIProxy, AlchemyPoint, Nginx, SafeSquid, Squid, and yProxy. Since each anonymizer works differently and comes with its own set of pros, cons, and risks, it is extremely important to see whether a specific anonymizer meets your specific needs.
What Are the Downsides and Risks of an Anonymizer?
While an anonymizer offers considerable benefit to end-users concerned about the risks mentioned above, it is not a "silver bullet" or a "privacy panacea." To start, an anonymizer is primarily a privacy tool, not a security tool (except insofar as sharing your IP address may increase your vulnerability to some cyber-attacks). In other words, an anonymizer does nothing to protect the integrity of your data as it is sent to and from the web server. Moreover, using an anonymizer may increase your vulnerability to a cross-site request forgery, cookie stealing, and, in particular, simple packet sniffing. Beyond the security risks to your data, anonymizers may increase a number of other potential privacy risks:
(1) Anonymizer Recordkeeping. If an anonymizing intermediary server is located within a country that requires ISPs and other service providers to keep records of traffic, your browsing habits are not invisible. The government or an authorized third party could subpoena or seize the history of your browsing activity from the anonymizer.
(2) Man in the Middle Attacks. By routing your traffic through intermediaries, you increase your exposure to man-in-the-middle attacks.
(3) Selling Browsing Records. An anonymizer could sell or provide unauthorized access to your browsing history. If you transmit sensitive unencrypted data through an anonymizer, you are taking a considerable security risk.
(4) Login-Based Records. Some web services such as Google's Web History record a significant amount of end-user behavior based upon voluntary user login. In other words, when logged in to your Google account, your Google search behavior (among other things) will be personally identifiable by Google-even if you are using an anonymizer.
(5) TCP Only. When most end-users access the Internet, they utilize many different services (e.g., email, Internet, teleconferencing) and these differing services often require different network protocols. "Packet sniffer" tools such as WireShark will let you examine the protocols and packets sent and received by your computer. Because many anonymizers do not handle non-TCP traffic, they would not anonymize other online activities such as Voice-over-IP phone calls.